Security Options: Single Sign-On
Use this screen to enable single sign-on parameters using SAML authentication for your firm.
This is a separate optional product and will not be available unless your firm is licensed for Single Sign-On. Please note that the following is for informational purposes only. To implement SSO, contact your account manager.
Warning! Do not change any of these settings unless you are certain of the correct values, or you may break your firm’s ability to login into the product!
The SSO configuration information is located on the Admin > Firm Configuration > Single Sign‐On tab.

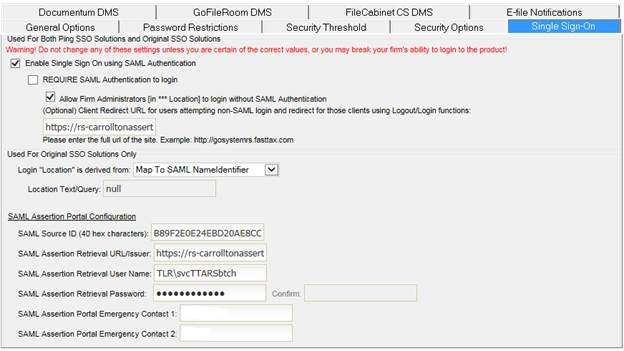
On the Single Sign‐On tab, note the following:
-
The box Enable Single Sign On using SAML Authentication is used to enable single sign-on access for the firm.
-
REQUIRE SAML Authentication to login forces all users to use SSO for product access. The login screen will redirect users to the URL entered in the (Optional) Client Redirect URL field, if supplied.
-
Allow Firm Administrators [in *** Location] to login without SAML Authentication allows *** location firm administrators to log into RS using the login page when the REQUIRE SAML Authentication to login is checked.
-
Login “Location” is derived from should always be set to Map To SAML NameIdentifier. This uses the Access > User > Single Sign-On tab > Unique SAML Subject NameIdentifier mapped to this user entry to the domain user account passed in by the assertion server during SSO login.
-
The bottom section after the SAML Assertion Portal Configuration label contains information specific to the client assertion server configuration.
-
The SAML Source ID (40 hex characters): contains a hash code assigned to a firm as a unique 40-character firm identifier (Source ID).
-
The URL in the SAML Assertion Retrieval URL/Issuer: field shows the client assertion server callback URL that the system calls when a user in the firm enters the product using SSO.
-
The SAML Assertion Retrieval User Name: field, usually populated by ssoassertionuser, shows the user name used with the assertion server callback.
-
The password in the SAML Assertion Retrieval Password: and Confirm: fields is the user password used with the assertion server callback. The implementation team that sets up your SSO will enter this for you.
-
The primary and secondary SSO contacts at the firm appears in the SAML Assertion Portal Emergency Contact 1 and SAML Assertion Portal Emergency Contact 2 fields.
Ping Federate SSO Configuration
Four steps are required for a client to use our Ping Federate SSO solution.
You must contact your account manager and purchase the SAML Single Sign-On product. This will appear in the Account Information page in the Products tab.
Complete the Federated Single Sign-On client handout form and return it to Thomson Reuters. The TRTA SSO Admin team will create an entry in the Ping Federate system using the information in the form.
Enable Single Sign-On in the Admin > Firm Configuration > Single Sign-On tab. Set the other options to support SSO functionality as the client needs.
The first time a user attempts to log in using the SSO system, the Ping Federate system will send the user to the RS authentication dialog page with an SSO token. RS will authenticate the user, call the Ping Federate system web service to notify Ping Federate that the user is authenticated, and pass the SSO token and product credentials. The Ping Federate service will save the user information in the database that creates the remote client user account to the RS user account. On all subsequent login attempts, Ping Federate will map the incoming user account to the RS user account, and the user will be passed straight into the product, if the user account is still active.
RS Resources/exp_security_5.htm/TY2021
Last Modified: 03/19/2020
Last System Build: 09/25/2022
©2021-2022 Thomson Reuters/Tax & Accounting.